Topic: SECURITY - on July 11, 2016 at 1:17:00 PM CEST
BND-Spionage unter Freunden: Dutzende Regierungsstellen im Visier
Kanzlerin Merkel hatte 2013 gesagt: "Ausspähen unter Freunden – das geht gar nicht." Dann wurde klar: Das geht doch. Kontrolleure des Bundestags haben nun ein Fazit gezogen und das birgt gehörig Sprengstoff. In der BND-Affäre um Spionage unter Freunden sind neue Details über den Umfang der bis Oktober 2013 laufenden Aktionen bekannt geworden. Nach einer der dpa vorliegenden Bewertung des Bundestagsgremiums zur Kontrolle der Geheimdienste (PKGr) wurde "eine niedrige zweistellige Zahl von Teilnehmern" abgehört, die Regierungen von EU- oder Nato-Ländern zuzuordnen sind. Darunter sind Staats- oder Regierungschefs und Minister, deren Umfeld – also der Amtssitz, der Stab oder das Büro – sowie militärische Einrichtungen. Es gehe um "mehrere Dutzend" solcher Fälle, erfuhr die dpa.
... Link (0 comments) ... Comment
Topic: SECURITY - on July 11, 2016 at 1:16:00 PM CEST
Do You Own Your Own Fingerprints?
An obscure law could lead to broader limits on biometrics. These days, many of us regularly feed pieces of ourselves into machines for convenience and security. Our fingerprints unlock our smartphones, and companies are experimenting with more novel biometric markers—voice, heartbeat, grip—as ID for banking and other transactions. But there are almost no laws in place to control how companies use such information. Nor is it clear what rights people have to protect scans of their retinas or the contours of their face from cataloging by the private sector.
... Link (0 comments) ... Comment
Topic: SECURITY - on July 9, 2016 at 5:53:00 PM CEST
NSA targets the privacy-conscious
The investigation discloses the following: Two servers in Germany - in Berlin and Nuremberg - are under surveillance by the NSA. Merely searching the web for the privacy-enhancing software tools outlined in the XKeyscore rules causes the NSA to mark and track the IP address of the person doing the search. Not only are German privacy software users tracked, but the source code shows that privacy software users worldwide are tracked by the NSA. Among the NSA's targets is the Tor network funded primarily by the US government to aid democracy advocates in authoritarian states. The XKeyscore rules reveal that the NSA tracks all connections to a server that hosts part of an anonymous email service at the MIT Computer Science and Artificial Intelligence Laboratory (CSAIL) in Cambridge, Massachusetts. It also records details about visits to a popular internet journal for Linux operating system users called "the Linux Journal - the Original Magazine of the Linux Community", and calls it an "extremist forum".
... Link (0 comments) ... Comment
Topic: SECURITY - on July 9, 2016 at 5:51:00 PM CEST
Quellcode entschlüsselt: Beweis für NSA-Spionage in Deutschland
Deutsche, die sich mit Verschlüsselung im Internet beschäftigen, werden gezielt vom US-Geheimdienst NSA ausgespäht. Anhand eines geheimen Quellcodes der NSA konnten WDR und NDR nun in Deutschland Opfer der NSA Überwachung namentlich identifizieren. Einer davon ist der Erlanger Student Sebastian Hahn, der sich in seiner Freizeit mit Anonymisierungstechnologie beschäftigt. Er ist nach Angela Merkel das erste namentlich bekannte Opfer der NSA.
... Link (0 comments) ... Comment
Topic: SECURITY - on July 8, 2016 at 4:57:00 PM CEST
NSA classifies Linux Journal readers, Tor and Tails Linux users as "extremists"
Are you a Linux Journal reader or use software such as Tor and Tails Linux? If so, you've probably been flagged as an "extremist" by the NSA. Leaked documents related to the XKeyscore snooping program reveal that the agency is targeting anyone who is interested in online privacy, specifically those who use the aforementioned software and visit the Linux user community website. XKeyscore is a collection and analysis software that was among a number of surveillance programs revealed by Edward Snowden last year. Its source code (basically a rule file), which has been obtained and analyzed by members of the Tor project and security specialists for German broadcasters NDR and WDR, identifies two German Tor Directory Authority servers as being under surveillance by the NSA. The code also cites a number of specific IP addresses of the Tor Directory Authority.
... Link (0 comments) ... Comment
Topic: SECURITY - on July 7, 2016 at 4:04:00 PM CEST
Here are the creeps who sell ATM skimmers on Alibaba
Last week I posted about a guy who came across a well-made skimmer at an ATM in Vienna. I wondered who made such a fine looking piece of sociopathic hardware. Turns out this company sells such devices in bulk via Alibaba.
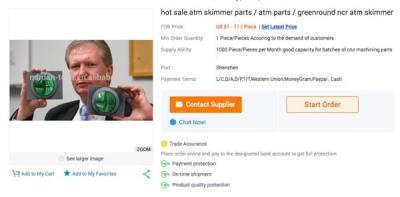
... Link (0 comments) ... Comment
Topic: SECURITY - on July 2, 2016 at 5:02:00 PM CEST
INTERVIEW | CRYPTOME: 1996/2016
"Cryptome welcomes documents for publication that are prohibited by governments worldwide, in particular material on freedom of expression, privacy, cryptology, dual-use technologies, national security, intelligence, and secret governance -- open, secret and classified documents -- but not limited to those. Documents are removed from this site only by order served directly by a US court having jurisdiction. No court order has ever been served; any order served will be published here -- or elsewhere if gagged by order. Bluffs will be published if comical but otherwise ignored. "
... Link (0 comments) ... Comment
Topic: SECURITY - on June 29, 2016 at 11:19:00 AM CEST
Secure-K is an encryped OS that lives on a USB drive
If you're looking for a encrypted, portable OS that can be securely loaded on any computer, Secure-K may be the answer. Also if you're afraid of hackers wearing hoodies in darkened rooms and find joy in a British man repeatedly saying "privacy" in an excited tone, you'll enjoy this video.
... Link (0 comments) ... Comment
Topic: SECURITY - on June 28, 2016 at 2:29:00 PM CEST
How a Kitten Video Can Transmit Secret Instructions to Criminals
An ancient form of information-hiding known as steganography has infiltrated the viral internet. Imagine your computer is infected. The virus that has infiltrated your machine commands it to perform tasks and open applications that you would normally use–except you’re not there to run them. At the same time every day, it launches Twitter, then generates user handles and hunts through tweets. It searches and waits until, bingo—it finds a recently tweeted link that leads to a photo of a flower. But, this is no ordinary photo. Laced into the Github image file’s long string of code are secret instructions that it needs to extract and upload information from your compromised computer to an internet cloud service set up by a hacker.
... Link (0 comments) ... Comment
Topic: SECURITY - on June 21, 2016 at 10:00:00 PM CEST
How Terrorists Use Encryption
Abstract: As powerful encryption increasingly becomes embedded in electronic devices and online messaging apps, Islamist terrorists are exploiting the technology to communicate securely and store information. Legislative efforts to help law enforcement agencies wrestle with the phenomenon of “going dark” will never lead to a return to the status quo ante, however. With the code underlying end-to-end encryption now widely available, unbreakable encryption is here to stay. However, the picture is not wholly bleak. While end-to-end encryption itself often cannot be broken, intelligence agencies have been able to hack the software on the ends and take advantage of users’ mistakes.
... Link (0 comments) ... Comment
Topic: SECURITY - on June 21, 2016 at 6:42:00 PM CEST
New 'Hardened' Tor Browser Protects Users From FBI Hacking
According to a new paper, security researchers are now working closely with the Tor Project to create a "hardened" version of the Tor Browser, implementing new anti-hacking techniques which could dramatically improve the anonymity of users and further frustrate the efforts of law enforcement... "Our solution significantly improves security over standard address space layout randomization (ASLR) techniques currently used by Firefox and other mainstream browsers," the researchers write in their paper, whose findings will be presented in July at the Privacy Enhancing Technologies Symposium in Darmstadt, Germany.
... Link (0 comments) ... Comment
Topic: SECURITY - on June 14, 2016 at 11:10:00 AM CEST
Olympic threats designed to trick you
Are you planning to visit Brazil during the Olympic Games? Or watch it online? In this blog post we discuss the threats to visitors aiming to travel to Brazil to watch the games and to those planning to watch it online. In the first part we’ll talk about phishing attacks, including one against the organizers of the Games; in the second we highlight WiFi security and the results of the wardriving we did on the streets of Rio, visiting the same places as tourists and the athletes. In the third and final part we touch upon physical security that involves the usage of USB charging spots at airports, the problem of credit card cloning and ATM skimmers that will directly affect visitors to this summer’s Olympic Games in Rio.
... Link (0 comments) ... Comment










