Topic: FUN - on June 22, 2016 at 9:25:00 PM CEST
Ленин — гриб - Lenin was a mushroom
Lenin was a mushroom (Russian: Ленин — гриб) was a highly influential televised hoax by Soviet musician Sergey Kuryokhin and reporter Sergey Sholokhov. It was first broadcast on 17 May 1991 on Leningrad Television.[1] The hoax took the form of an interview on the television program Pyatoe Koleso (The Fifth Wheel). In the interview, Kuryokhin, impersonating a historian, narrated his findings that Vladimir Lenin consumed large quantities of psychedelic mushrooms and eventually became a mushroom himself. Kuryokhin arrived at his conclusion through a long series of logical fallacies and appeals to the authority of various "sources" (such as Carlos Castaneda, the Massachusetts Institute of Technology, and Konstantin Tsiolkovsky), creating the illusion of a reasoned and plausible logical chain.
... Link
Topic: WEB - on June 22, 2016 at 9:22:00 PM CEST
Crims set up fake companies to hoard and sell IPv4 addresses
IPv4 addresses are now so valuable that criminals are setting up shell companies so they can apply for addresses, then resell them to users desperate to grow their networks. Criminals are doing so because there are no more IPv4 addresses left: the American Registry for Internet Numbers (ARIN) ran out in September 2015. ARIN maintains a waiting list for address buyers and also oversees a market for used IPv4 addresses. While it is conceivable that some users will hand back addresses they no longer require, the IPv4 transfer market is short of stock.
... Link (0 comments) ... Comment
Topic: STRANGE - on June 22, 2016 at 9:20:00 PM CEST
Sweden asks to meet Julian Assange inside Ecuador embassy
Ecuador has received a formal request from the Swedish authorities to interview Julian Assange, inside its London embassy, in a potential breakthrough to the long-running saga. The WikiLeaks founder, 44, is wanted for questioning over a 2010 rape allegation in Sweden, which he has always denied. He has been living inside Ecuador’s UK mission for four years in a bid to avoid extradition to Sweden, saying he fears he would then be transferred to the US to face political charges for orchestrating leaks of diplomatic cables.
... Link (0 comments) ... Comment
Topic: SCIENCE - on June 22, 2016 at 6:26:00 PM CEST
How Quantum Mechanics Could Be Even Weirder
And what it could mean for the future of computing
Why doesn’t the world make sense? At the fundamental level of atoms and subatomic particles, the familiar “classical” physics that accounts for how objects move around gives way to quantum physics, with new rules that defy intuition. Traditionally these are expressed as paradoxes: particles that can be in two places at once, cats that are simultaneously alive and dead, apparently impossible faster-than-light signaling between distant particles. But quantum rules are perfectly logical and consistent—the “paradoxes” are the result of our trying to impose on them the everyday reasoning of classical physics.
... Link (0 comments) ... Comment
Topic: EU - on June 22, 2016 at 6:18:00 PM CEST
Europe Will Spend €1 Billion to Turn Quantum Physics Into Quantum Technology
A 10-year-long megaproject will go beyond quantum computing and cryptography to advance other emerging technologies. European quantum physicists have done some amazing things over the past few decades: sent single photons to Earth orbit and back, created quantum bits that will be at the heart of computers that can crack today’s encryption, and “teleported” the quantum states of photons, electrons, and atoms. But they’ve had less success at turning the science into technology. At least that’s the feeling of some 3,400 scientists who signed the “Quantum Manifesto,” which calls for a big European project to support and coordinate quantum-tech R&D. The European Commission heard them, and answered in May with a €1 billion, 10-year-long megaproject called the Quantum Technology Flagship, to begin in 2018. “Europe had two choices: either band together and compete, or forget the whole thing and let others capitalize on research done in Europe,” says Anton Zeilinger, a physicist at the University of Vienna who did breakthrough work in quantum teleportation, which would be key to a future Internet secured by quantum physics.
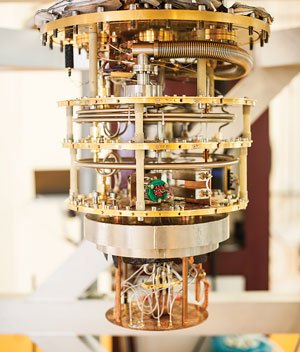
... Link (0 comments) ... Comment
Topic: WEB - on June 22, 2016 at 6:16:00 PM CEST
Revealed: US spy operation that manipulates social media
Military's 'sock puppet' software creates fake online identities to spread pro-American propaganda. The US military is developing software that will let it secretly manipulate social media sites by using fake online personas to influence internet conversations and spread pro-American propaganda. A Californian corporation has been awarded a contract with United States Central Command (Centcom), which oversees US armed operations in the Middle East and Central Asia, to develop what is described as an "online persona management service" that will allow one US serviceman or woman to control up to 10 separate identities based all over the world.
... Link (0 comments) ... Comment
Topic: War and Peace News - on June 22, 2016 at 6:14:00 PM CEST
There’s a new tool to take down terrorism images online. But social-media companies are wary of it.
President Obama suggested that extremist information spread online inspired a Florida man to commit the deadliest mass shooting in U.S. history at a gay nightclub in Orlando last week — the latest in a long line of terrorist attacks in which Islamist propaganda played some role in radicalizing the assailant. Now a Dartmouth College researcher and a nonprofit group say they have created a technology that can help Internet companies instantly detect images and videos generated by terrorists and their supporters and remove them from their platforms.
... Link (0 comments) ... Comment
Topic: EU - on June 22, 2016 at 12:02:00 PM CEST
Beim Brexit dürfte das Parlament das Volk ignorieren - Nichts wird am 23. Juni endgültig entschieden
Die Mehrheit der britischen Abgeordneten ist gegen den Brexit – und darf den Willen des Volkes durchaus ignorieren. Es wäre nicht das erste Mal, dass das Parlament sich seinen Wählern widersetzt. In der Aufregung um das britische Referendum ist ein wichtiger Mitspieler völlig übersehen worden: das Parlament. Der Premierminister mag sich an das Ergebnis des 23. Juni gebunden fühlen und die "Instruktion" des Volkes, wie er es nennt, ausführen. Aber die Verfassung besagt etwas anderes: Hoheit über das, was passiert, hat nicht die Regierung, sondern das Parlament.
... Link (0 comments) ... Comment
Topic: War and Peace - on June 22, 2016 at 11:45:00 AM CEST
When Kodak Accidentally Discovered A-Bomb Testing
The ground shook, a brilliant white flash enveloped the sky, and the world changed forever. Code name "Trinity," the bomb test at dawn on July 16, 1945 in Alamogordo, New Mexico was the first large-scale atomic weapons testing in history. Only three weeks later two atomic bombs were dropped on Japan. More than 1,900 miles away from Alamogordo, at the Rochester, NY headquarters of Eastman Kodak, a flood of complaints came in from business customers who had recently purchased sensitive X-ray film from the company. Black exposed spots on the film, or "fogging," had rendered it unusable. This perplexed many Kodak scientists, who had gone to great lengths to prevent contaminations like this.
... Link (0 comments) ... Comment
Topic: logisch - on June 22, 2016 at 11:43:00 AM CEST
Refugees in Greece need internet so badly that they’ll stop a riot to let the wifi guys work
Kevin MacRitchie surveyed the inferno spreading across Diavata refugee camp. From his vantage point on the roof, where he had been fixing a satellite dish, he could see a column of thick black smoke twisting toward the sky above two rows of incinerated tents. While Greek army and police helped battle the fire, a protest had erupted at the front gate, by Syrian refugees frustrated with conditions in the camp and the asylum backlog that was keeping them there. That meant MacRitchie was now alone. His teammate, David Tagliani, had run out to drive their equipment van into the camp, and in the meantime, the angry mass had blocked the entrance. Yet when they recognized Tagliani behind the wheel, the protestors stopped. “Wifi,” they called to each other, “wifi.” And they cleared a path to let the van pass.
... Link (0 comments) ... Comment
Topic: DRUGS - on June 22, 2016 at 11:41:00 AM CEST
How 'Deleted' Yahoo Emails Led to a 20-Year Drug Trafficking Conviction
In 2009, Russell Knaggs, from Yorkshire, England, orchestrated a plan to import five tonnes of cocaine from South America hidden in boxes of fruit. Somehow, he did this all from the cell of a UK prison, while serving a 16-year sentence for another drug crime. As part of the plan, a collaborator in Colombia would log into a Yahoo email account and write a message as a draft. Another accomplice in Europe would read the message, delete it, and then write his own. The point of this was to avoid creating any emails that could be found by law enforcement.
... Link (0 comments) ... Comment
Topic: DRUGS - on June 22, 2016 at 11:39:00 AM CEST
On Legalizing Medical Cannabis: The DEA Responds
The DEA wants to remove the barriers to cannabis research, a spokesman told aNewDomain in a lengthy interview today. But how and when will it reschedule cannabis as a Schedule II drug? [Exclusive]
A DEA official responded at length today to a widely-circulated report that the DEA plans to effectively legalize medical cannabis this August. In an interview with aNewDomain today, DEA staff coordinator Russ Baer wouldn’t confirm the Santa Monica Observer report that the DEA will reschedule cannabis as a prescription-only Schedule II drug on Aug. 1, 2016. But he did comment at length about the agency’s thoughts around legalizing medical cannabis and how rescheduling cannabis from its current Schedule I status would have to work.
... Link (0 comments) ... Comment










