Topic: SECURITY - on February 21, 2009 at 12:06:00 PM CET
State bill would turn RFID researchers into felons
The sponsor of a controversial bill before the Nevada legislature has promised to introduce amendments after security experts and civil libertarians warned it would make felons of people studying privacy threats involving RFID, or radio frequency identification.
In its present form, Senate Bill 125 (PDF) would make it a felony for anyone to possess, read or capture the personally identifying RFID information of others without their consent. Without changes, the legislation would prevent the testing and demonstrating of RFID weaknesses in a state that hosts Defcon and Black Hat, the biggest hacker conference and one of the biggest security conferences respectively.
... Link (0 comments) ... Comment
Topic: SECURITY - on February 2, 2009 at 11:00:00 AM CET
Passport RFIDs cloned wholesale by $250 eBay auction spree
Using inexpensive off-the-shelf components, an information security expert has built a mobile platform that can clone large numbers of the unique electronic identifiers used in US passport cards and next generation drivers licenses.
The $250 proof-of-concept device - which researcher Chris Paget built in his spare time - operates out of his vehicle and contains everything needed to sniff and then clone RFID, or radio frequency identification, tags. During a recent 20-minute drive in downtown San Francisco, it successfully copied the RFID tags of two passport cards without the knowledge of their owners.
... Link (0 comments) ... Comment
Topic: SECURITY - on November 30, 2008 at 1:04:51 PM CET
No scanners to read ID cards
Britain's first ID cards, issued last week with fingerprint and facial details, cannot be read by any official body because the government has not issued a single scanner.
... Link (0 comments) ... Comment
Topic: SECURITY - on November 20, 2008 at 4:38:30 PM CET
US Army bans USB devices to contain worm
The US Army has reportedly suspended the use of USB and removable media devices after a worm began spreading across its network.
Use of USB drives, floppy discs, CDs, external drives, flash media cards and all other removable media devices has been placed on hold in order to contain the spread of Agent-BTZ, a variant of the SillyFDC worm, Wired reports. Such a temporary ban would cause inconvenience in any organisation, but for the US military it's an even more serious problem because in many locations email or online transfer of files are not viable options.
... Link (0 comments) ... Comment
Topic: SECURITY - on November 2, 2008 at 4:36:00 PM CET
Virtual Heist Nets 500,000+ Bank, Credit Accounts
A single cyber crime group has stolen more than a half million bank, credit and debit card accounts over the past two-and-a-half years using one of the most advanced strains of computer spyware in existence, according to research to be published today. The discovery is among the largest stolen data caches ever recovered.
Researchers at RSA's FraudAction Research Lab unearthed the massive trove of purloined data while tracking the activities of a family of spyware known as the "Sinowal" Trojan, designed to steal data from Microsoft Windows PCs.
... Link (0 comments) ... Comment
Topic: SECURITY - on October 23, 2008 at 2:42:00 PM CEST
Blackwater has a warship?
BLACKWATER Worldwide — the US private military contractor embroiled in controversy over its actions in Iraq — has sent a private sector warship equipped with helicopters to the Gulf of Aden, and is offering its services to shipowners concerned with Somali piracy.
The vessel, McArthur, is described as a multipurpose unit designed to support military and law-enforcement training, peace-keeping and stability operations.
... Link (0 comments) ... Comment
Topic: SECURITY - on October 19, 2008 at 2:57:00 PM CEST
Complete Spy Cam Smaller Than an Eyeball
The worlds smallest spy camera and dvr. This all in one package is the world’s first DVR and camera complete in the shape of a ball. Inside this Ping Pong size ball is a motion activated camera and DVR (digital video recorder) it captures images at 30 FPS at 320x240 resolutions. Comes with 128mb internal memory and supports up to a 2gig micro sd card. It can be used in various applications such as vehicle security, sports, personal security or whatever the user can dream up. This camera is an excellent tool for the private investigator. Now you can literally carry a portable video recorder where ever you subject goes, now you will be able to obtain video in place where your camcorder or you body worn video are useless. Just hold it in your hand its that small!

... Link (0 comments) ... Comment
Topic: SECURITY - on October 18, 2008 at 1:51:00 PM CEST
DHS perfects the abusive EULA
Check out the EULA for the Department of Homeland Security's web page for applying for travel visa waivers!
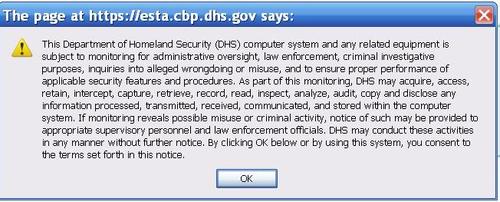
... Link (0 comments) ... Comment
Topic: SECURITY - on October 13, 2008 at 3:35:00 PM CEST
World Bank denies hackers pwned key systems
The World Bank has denied reports that hackers penetrated its network on multiple occasions over the last year.
Fox News reports the financial institution has suffered at least six attacks since the middle of 2007. The assault emerged in the course of a separate FBI investigation, prompting the bank to issue a memo (pdf) to warn workers.
... Link (0 comments) ... Comment
Topic: SECURITY - on October 12, 2008 at 12:50:00 PM CEST
The coverage of the recent NSA intercept stories has some serious deficiencies. - Inside Operation Highlander: the NSA's Wiretapping of Americans Abroad
That's not the Terrorist Surveillance Program (TSP), and not related to foreign intelligence collection programs in that were in place in the United States. That's the NSA working in a foreign military operations theater, and is vastly different. These intercepts were happening in realtime and were focused on an area of military operations.
When working in the dynamic environment of an operations theater, it's difficult to make distinctions about what traffic should be monitored and when. That is of course not to say that US Persons should continue to be collected on after their status is known, even under difficult circumstances.
... Link (0 comments) ... Comment
Topic: SECURITY - on October 12, 2008 at 12:48:00 PM CEST
World Bank Under Cyber Siege in 'Unprecedented Crisis'
The World Bank Group's computer network — one of the largest repositories of sensitive data about the economies of every nation — has been raided repeatedly by outsiders for more than a year, FOX News has learned.
It is still not known how much information was stolen. But sources inside the bank confirm that servers in the institution's highly-restricted treasury unit were deeply penetrated with spy software last April. Invaders also had full access to the rest of the bank's network for nearly a month in June and July.
... Link (0 comments) ... Comment
Topic: SECURITY - on October 12, 2008 at 12:46:00 PM CEST
Turbo-charged wireless hacks threaten networks
The latest graphics cards have been used to break Wi-Fi encryption far quicker than was previously possible. Some security consultants are already suggesting the development blows Wi-Fi security out of the water and that corporations ought to apply tighter VPN controls, or abandon wireless networks altogether, in response.
Russian firm ElcomSoft has applied GPU acceleration technology to its password recovery tool to allow PCs or servers running supported NVIDIA video cards to break Wi-Fi encryption up to 100 times faster than is possible by using conventional microprocessors. Recovery times for Wi-Fi keys are increased by a factor between 10 to 15 in the use of Elcomsoft Distributed Password Recovery in combination with a regular laptop featuring NVIDIA GeForce 8800M or 9800M series GPUs.
... Link (0 comments) ... Comment










