Topic: SECURITY - on July 31, 2009 at 12:05:00 PM CEST
Bootkit hebelt Festplattenverschlüsselung aus
Der österreichische IT-Sicherheitsspezialist Peter Kleissner hat auf der Sicherheitskonferenz Black Hat ein Bootkit namens Stoned demonstriert, das in der Lage ist TrueCrypts vollständige Partitions- und Systemverschlüsselung auszuhebeln. Bootkits sind eine Kombination aus einem Rootkit und der Fähigkeit des Schädlings, den Master Boot Record des PC zu modifizieren und so bereits vor dem Start des Betriebssystems aktiv zu werden.
... Link
Topic: SECURITY - on July 14, 2009 at 12:32:00 PM CEST
How to use electrical outlets and cheap lasers to steal data
If attackers intent on data theft can tap into an electrical socket near a computer or if they can draw a bead on the machine with a laser, they can steal whatever is being typed into it.
How to execute these attacks will be demonstrated at the Black Hat USA 2009 security conference in Las Vegas later this month by Andrea Barisani and Daniele Bianco, a pair of researchers for network security consultancy Inverse Path.
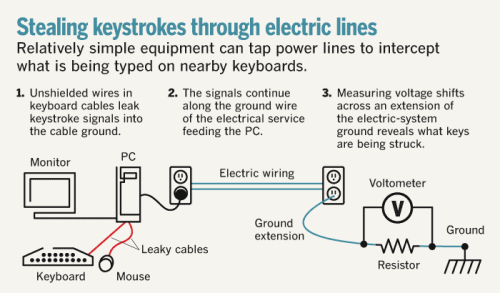
... Link
Topic: SECURITY - on July 4, 2009 at 1:42:00 PM CEST
4th of July Security Awareness
In the United States, Independence Day, commonly known as the Fourth of July, is a federal holiday commemorating the adoption of the Declaration of Independence on July 4, 1776, declaring independence from the Kingdom of Great Britain. Independence Day is commonly associated with fireworks, parades, barbecues, carnivals, fairs, picnics, concerts, baseball games, political speeches and ceremonies, and various other public and private events celebrating the history, government, and traditions of the United States. Independence Day is the national day of the United States.
... Link
Topic: SECURITY - on July 4, 2009 at 1:17:00 PM CEST
Professor Gets 4 Years in Prison for Sharing Drone Plans With Students
Retired University of Tennessee Professor Dr. John Reece Roth has been sentenced to four years in prison after he allowed a Chinese graduate student to see sensitive information on Unmanned Air Vehicles (UAVs), also known as drones.
... Link
Topic: SECURITY - on June 30, 2009 at 11:27:00 AM CEST
America's Fortress: Cheyenne Mountain, NORAD live on
If there are two things that drive the folks at the world-famous Cheyenne Mountain complex crazy, it's the widely held public perceptions that, for one, the complex has shut down altogether, and that it is synonymous with NORAD, the North American Aerospace Defense Command.
... Link
Topic: SECURITY - on May 31, 2009 at 12:56:00 PM CEST
L0phtcrack ist zurück
Statt der Rückkehr des Duke gibt es nun die Rückkehr des legendären Passwortcrackers L0phtcrack – und zwar in Version 6. Nach dem Kauf des unter anderem aus den L0pht Heavy Industries hervorgegangenen Unternehmens @stake durch Symantec war L0phtcrack vom Markt verschwunden. Das ehemalige L0phtcrack-Team aus Christien Rioux, Chris Wysopal und Peiter Zatkhat (Mudge) hat Anfang des Jahres die Rechte an dem Tool von Symantec zurückgekauft und es weiterentwickelt.
... Link
Topic: SECURITY - on May 31, 2009 at 12:50:00 PM CEST
L0phtCrack (v6) Rises Again
L0phtCrack — now 12 years old — used to be a security 'tool of choice' for black hats, pen-testers, and security auditors alike — that is, until it was sold by L0pht to @stake, then Symantec, to be released and subsequently dropped as LC 5. As an IT security consultant, I used this tool to regularly expose vulnerabilities or recover data when there were few other options available. Eventually, I let it go as tech evolved away. Now, after being returned to its original developers, version 6 was released this week with fresh features: support for 64-bit multiprocessors, (current) Unix and Windows operating systems, and a number of other features, including enhanced handling of NTLM password hashes and support for rainbow tables. Interested parties, especially consultants, will find this shiny new version sports a hefty price tag. It raises doubts in my mind whether it can effectively compete with open source alternatives that go by similar names, but as I found earlier versions so useful, its re-emergence seems worth the mention.
... Link
Topic: SECURITY - on May 6, 2009 at 3:10:00 PM CEST
Hackers demand $10m ransom for Virginia medical data
Almost 8.3 million patient records have been stolen from a Virginia government website that tracks prescription drug abuse, according to hackers who are demanding a $10 million ransom for their return.
"I have your shit!" the note, which was posted to Wikileaks read. "In my possession, right now, are 8,257,378 patient records and a total of 35,548,087 prescriptions. Also, I made an encrypted backup and deleted the original. Unfortunately for Virginia, their backups seem to have gone missing, too."
... Link
Topic: SECURITY - on April 24, 2009 at 11:38:00 AM CEST
Take That! High-Tech Ways To Fight Off Pirates
Modern pirates are creating a market for modern pirate repellents.
The owners of ships that ply the dangerous waters near Somalia are looking at options including slippery foam, lasers, electric fences, water cannons and high-intensity sound.
... Link
Topic: SECURITY - on March 26, 2009 at 12:49:00 PM CET
Pentagon hacker Analyzer suspected of $10m cyberheist
Charges against notorious hacker-turned-suspected-cyber-fraudster Ehud Tenenbaum have expanded to include alleged fraud involving banks and credit card firms in both Canada and the US.
Ehud Tenenbaum (AKA The Analyzer), 29, was arrested in Canada last September on suspicion he conspired with others to hack into the systems of a financial service companies, before transferring funds into pre-paid debit card accounts under the control of a cyberfraud crew. The group subsequently cashed out these accounts, making an estimated $1.5m in the process.
... Link (0 comments) ... Comment
Topic: SECURITY - on March 26, 2009 at 12:44:00 PM CET
German Authorities Raid Home Looking For Wikileaks Info
In just a short while, Wikileaks has proven to be both an amazing resource to reveal useful information and a massive thorn in the side of those who wish that info wasn't revealed (this includes, by the way, Wikileaks itself, which had to deal with some of its own private info that was leaked as well.
... Link (0 comments) ... Comment
Topic: SECURITY - on March 25, 2009 at 2:42:00 PM CET
Hausdurchsuchung bei Wikileaks.de?
Gerade vermeldet Wikileaks auf Twitter, dass es eine “Gefahr im Verzug”-Hausdurchsuchung beim Domaininhaber von Wikileaks.de gegeben haben soll. Dieser sitzt laut Denic in Dresden. Als Grund wurden nur kurz “Internet-Zensurlisten” angegeben und weitere Informationen angekündigt: “Stay tuned”.
netzpolitik.org wikinews.org Das Interview nach der Hausdurchsuchung von Wikileaks.de
... Link (0 comments) ... Comment










