Topic: SECURITY - on September 27, 2011 at 8:34:00 AM CEST
Tor-ramdisk
Tor-ramdisk is an i686 uClibc-based micro Linux distribution whose sole purpose is to securely host a Tor server purely in RAM. For those not familiar with Tor, it is a system which allows the user to construct encrypted virtual tunnels which are randomly relayed between Tor servers (nodes) until the connection finally exits to its destination on the internet. The encryption and random relaying resist traffic analysis in that a malicious sniffer cannot easily discover where the traffic is coming from or what data it contains. While not perfect in its efforts to provide users with anonymity, Tor does help protect against unscrupulous companies, individuals or agencies from "watching us".
... Link (0 comments) ... Comment
Topic: SECURITY - on September 25, 2011 at 10:59:00 AM CEST
TSA Scanners Can’t Seem to Detect Your Concealed Weapons Through Shiny Clothes
It never stops. Caught somewhere between hilarious and infuriating, Marilyn W. Thompson with the Washington Post discovered that her shiny shirt prevented the roughly $150,000 TSA scanner from doing its job. You mean wearing my late-90s shiny suit means EXTRA gropings??
Thompson remarked on her confusion that these scanners can pick up bladed weapons and ass explosives but can't handle a shiny shirt from Banana Republic.
... Link (0 comments) ... Comment
Topic: SECURITY - on September 3, 2011 at 9:06:00 AM CEST
FBI / IFPI Teach How To Bust Private Torrent Sites
A diplomatic cable recently published by Wikileaks reveals how the U.S. Government has spent $125,000 to educate Ukraine’s police officers on Internet piracy. Among other things, experts from the FBI and IFPI taught 30 of Ukraine’s top cyber-crime officers how to bust private torrent sites. Whether the investment will pay off is doubtful though, as some police officers said that they have no Internet connection at their workplace.
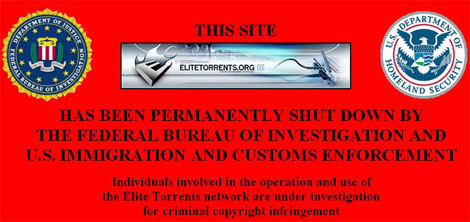
... Link (0 comments) ... Comment
Topic: SECURITY - on August 18, 2011 at 11:54:00 AM CEST
Security flaw found in feds' digital radios
Expensive high-tech digital radios used by the FBI, Secret Service, and Homeland Security are designed so poorly that they can be jammed by a $30 children's toy, CNET has learned.
A GirlTech IMME, Mattel's pink instant-messaging device with a miniature keyboard that's marketed to pre-teen girls, can be used to disrupt sensitive radio communications used by every major federal law enforcement agency, a team of security researchers from the University of Pennsylvania is planning to announce tomorrow.
... Link (0 comments) ... Comment
Topic: SECURITY - on August 15, 2011 at 2:05:00 PM CEST
Chaos Computer Club wirft Domscheit-Berg raus
Zoff zwischen dem Hacker-Verein CCC und Wikileaks-Aussteiger Domscheit-Berg: Der Vorstand schließt den Gründer der Plattform Openleaks aus, er habe den Ruf des Vereins ausgenutzt. Domscheit-Berg reagiert mit Unverständnis.
... Link (0 comments) ... Comment
Topic: SECURITY - on August 14, 2011 at 9:38:00 AM CEST
THC-IPV6 - v1.8 - CCC Camp release
A complete tool set to attack the inherent protocol weaknesses of IPV6 and ICMP6, and includes an easy to use packet factory library.
[0x00] News and Changelog
Please note that public versions do not include all tools available!
Only those who send in comprehensive patches and new tools for thc-ipv6 get the private
versions which are released more often, include unreleased tools and more!
If you want to participate, here is a list of tools that would be interesting:
* Adding raw mode (sending into a sit 6to4 tunnel) to the library (the current implemetation doesnt work)
* Enhancing the library so it works on FreeBSD and OSX too
* Create a tool which tests an ipv6 address if it is an endpoint for various tunnel protocols
* Adding more exploit tests to exploit6 (I can supply a long list of exploit files)
* Adding more denial of service tests to denial6
* Add a dhcp6 client fuzzer
* Add a dhcp6 server fuzzer
If you want to work on a topic on the list, email me, so not multiple people are working on the same tool.
Next Trainings: DeepSec, Vienna, 15-16th November 2011, "Pentesting & and Securing IPv6 Networks" CanSecWest, Vancouver, 5-6th March 2012, "Pentesting & and Securing IPv6 Networks"
... Link (0 comments) ... Comment
Topic: SECURITY - on August 9, 2011 at 10:49:00 AM CEST
Stromnetze: Der Hacker kommt durch die Hintertür
Auf der Black-Hat-Sicherheitskonferenz in Las Vegas zeigten Hacker, wie man in Siemens-Industriesteuerungen und SAP-Systeme eindringt. Beides sind zentrale Komponenten des "intelligenten" Stromnetzes in Österreich.
In ihren Grundzügen waren die Sicherheitslöcher bereits seit Mai bekannt und hätten auch schon da auf der Security-Konferenz "TakeDown" im Detail veröffentlicht werden sollen.
... Link (0 comments) ... Comment
Topic: SECURITY - on July 26, 2011 at 9:14:00 AM CEST
Wir schützen unsere Freiheit nicht, indem wir sie abschaffen
Es ist wirklich unglaublich: Die CDU/CSU-Fraktion nutzt die Anschläge in Norwegen aus und instrumentalisiert die Opfer von Oslo und Utøya für ihre sinnlose Forderung nach mehr Überwachung der gesamten Gesellschaft. Der innenpolitische Sprecher der CDU/CSU im Bundestag, Hans-Peter Uhl, fordert heute öffentlich mit Verweis auf Norwegen die Wiedereinführung einer Kommunikations-Vorratsdatenspeicherung, also dass von allen Menschen ohne irgendeinen Verdacht pauschal und auf Vorrat (sprich ins Blaue hinein) gespeichert werden solle, wer mit wem telefoniert, SMS oder E-Mail schreibt, wo man sich dabei befindet und wer mit welcher IP-Adresse im Netz surft.
... Link (0 comments) ... Comment
Topic: SECURITY - on June 17, 2011 at 10:10:00 AM CEST
NSA $3.2 Billion “Site M” Expansion Planning Documents Reveal Cyberwar Command Center
In July 2010, the NSA revealed that it was expanding into a 227-acre parcel of land at Fort Meade called “Site M”, constructing a series of buildings that could cost as much as $5.2 billion. This expansion would displace two golf courses currently occupying the land and provide the NSA, which already occupies 630 acres at Fort Meade, with more space to build “an operational complex and to construct and operate consolidated facilities to meet the National Security Agency’s (NSA) continually evolving requirements and for Intelligence Community use”. The project has been shrouded in secrecy throughout its existence and there are only a few references to “Site M” in DoD budget planning documents. However, a recently discovered collection of development planning documents for the Site M project provide detailed information about the proposed $3.2 billion expansion, indicating that the facility will be a centralized command center for the NSA’s evolving cyberwarfare capabilities.

publicintelligence.net NSA “Site M” Expansion Planning Documents
... Link (0 comments) ... Comment
Topic: SECURITY - on June 10, 2011 at 8:31:00 AM CEST
A Primer on Wikileaks Espionage on TOR Exit Nodes
In 2007, Dan Egerstad, Swedish security researcher, exposed how the Tor network could easily be used for intelligence gathering: [1]
``Dan Egerstad is a Swedish security researcher; he ran five Tor nodes. Last month, he posted a list of 100 e-mail credentials -- server IP addresses, e-mail accounts and the corresponding passwords -- for embassies and government ministries around the globe, all obtained by sniffing exit traffic for usernames and passwords of e-mail servers.''
... Link (0 comments) ... Comment
Topic: SECURITY - on June 9, 2011 at 9:54:00 AM CEST
NATO: Anonymous will be "infiltrated" and "persecuted"
The North Atlantic Treaty Organization contains the combined military might of 28 member countries, including Germany, the United Kingdom, and France. All three of those nations, and the United States, possess huge armies, nuclear weapons, and are committed to Article Five of NATO's charter:
The Parties agree that an armed attack against one or more of them in Europe or North America shall be considered an attack against them all and consequently they agree that, if such an armed attack occurs, each of them, in exercise of the right of individual or collective self-defence recognised by Article 51 of the Charter of the United Nations, will assist the Party or Parties so attacked.
... Link (0 comments) ... Comment
Topic: SECURITY - on March 31, 2011 at 10:04:00 AM CEST
Berlusconi calls George Clooney to his defence - Sex trial witness request 'odd', admits Hollywood star
Italian Prime Minister Silvio Berlusconi has called Hollywood star George Clooney among his defense witnesses when he goes on trial next month accused of sleeping with an under-aged prostitute, court documents said.
... Link (0 comments) ... Comment










