Topic: SECURITY - on November 21, 2011 at 10:10:00 AM CET
The Surveillance Catalog - Where governments get their tools
Documents obtained by The Wall Street Journal open a rare window into a new global market for the off-the-shelf surveillance technology that has arisen in the decade since the terrorist attacks of Sept. 11, 2001.
The techniques described in the trove of 200-plus marketing documents include hacking tools that enable governments to break into people’s computers and cellphones, and "massive intercept" gear that can gather all Internet communications in a country.
The documents—the highlights of which are cataloged and searchable here—were obtained from attendees of a secretive surveillance conference held near Washington, D.C., last month
... Link (0 comments) ... Comment
Topic: SECURITY - on November 20, 2011 at 11:58:00 AM CET
Foreign hackers hit public water system
A cyber strike launched from outside the US has hit a public water system in Illinois, an expert on infrastructure control systems says.
''This is arguably the first case where we have had a hack of critical infrastructure from outside the United States that caused damage,'' a managing partner at Applied Control Solutions, Joseph Weiss, said.
''That is what is so big about this,'' he continued. ''They could have done anything because they had access to the master station.''
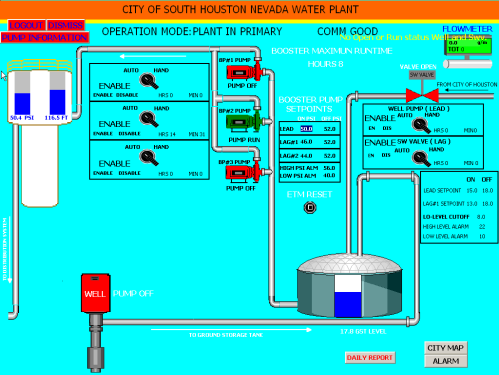
Hacker says he broke into Texas water plant, others Water utility hackers destroy pump, expert says theage.com.au pr0f
... Link (0 comments) ... Comment
Topic: SECURITY - on November 20, 2011 at 11:39:00 AM CET
Full disk encryption is too good, says US intelligence agency
You might be shocked to learn this, but when a quivering-lipped Chloe from 24 cracks the encryption on a terrorist’s hard drive in 30 seconds, the TV show is faking it. “So what? It’s just a TV show.” Well, yes, but it turns out that real federal intelligence agencies, like the FBI, CIA, and NSA, also have a problem cracking encrypted hard disks — and according to a new research paper, this is a serious risk to national security.
... Link (0 comments) ... Comment
Topic: SECURITY - on November 18, 2011 at 4:26:00 PM CET
Botnets - Herds of Internet Creatures Running Amuck
Remember the 1999 Sci-Fi classic movie, The Matrix, where Earth had been taken over by machines that created a simulated reality in order to control the human population? The human race deliberately created a sentient network of computers for the good of mankind. As energy became scarce, however, the computer network created a simulated reality to mentally enslave the human population; using human body heat and electrical activity as an energy source.
... Link (0 comments) ... Comment
Topic: SECURITY - on November 12, 2011 at 5:18:00 PM CET
Mikko Hypponen Warns of Adobe Reader Threats
F-Secure's Mikko Hypponen urged organizations to reconsider the continued use of Adobe Reader given the tendency for attackers to exploit the application's frequent vulnerabilities.
Hypponen made the comments during the recent PacSec 2011 conference in Tokyo.
Attackers often exploit a vulnerabilities that allows malicious code to be embedded in a PDF file, which then infects the victim's computer and can create a backdoor that hackers can use to access systems and glean sensitive information.
But Hypponen says that it is not the PDF format that is the culprit, but instead it is the wide spread use of Adobe Reader that provides the attackers with the opportunity to infect a system.
"These attacks are not against PDF - these attacks are against Adobe Reader. You open this files in any other reader than Adobe Reader and there is no exploit," said Hypponen.
... Link (0 comments) ... Comment
Topic: SECURITY - on November 9, 2011 at 8:38:00 AM CET
Cyber Fast Track (CFT)
The Defense Advanced Research Projects Agency's Cyber Fast Track program is aimed at improving Cyber Security. This program will rely on the skills of small organizations, boutiques, hacker spaces and maker labs to address cyber security issues.
According to DARPA program manager, Peiter "Mudge" Zatko, instead of engaging in traditional programs that don't produce results for years, we envision results within months by harnessing teams or individuals on the back of short, fixed-price DARPA contracts.
... Link (0 comments) ... Comment
Topic: SECURITY - on November 3, 2011 at 1:54:00 PM CET
Not enough evidence to link DuQu to Stuxnet: New Duqu Trojan analysis questions Stuxnet connection
New analysis of the Duqu Trojan has concluded there is not enough evidence to link it to Stuxnet, and calls early analysis that claimed Duqu was a new version of the worm pure speculation.
The facts observed through software analysis are inconclusive at publication time in terms of proving a direct relationship between Duqu and Stuxnet at any other level.
Dell SecureWorks CTU
The Duqu Trojan report, issued by the Dell SecureWorks Counter Threat Unit, said Duqu raised eyebrows recently for containing code that shares striking similarities as the Stuxnet worm , but ultimately the new Trojan was designed for a completely different purpose. The payloads of Duqu and Stuxnet are significantly different and unrelated, the Dell SecureWorks researchers said.
... Link (0 comments) ... Comment
Topic: SECURITY - on October 12, 2011 at 10:32:00 AM CEST
Kunden, die Staatstrojaner kauften, kauften auch Atomkraftwerke, Hartz4, Netzsperren, Wahlcomputer und anonyme Spenden
Es wäre langsam Zeit, daß sich Bundesstaatsanwaltschaft und Verfassungsgericht der Rechtsverstöße im behördlichen Umfeld annehmen.
via TweetDeck
... Link (0 comments) ... Comment
Topic: SECURITY - on October 12, 2011 at 10:01:00 AM CEST
More Info on German State Backdoor: Case R2D2
Last weekend, the German based Chaos Computer Club (CCC) published details on a backdoor trojan they claimed was being used by German authorities, in violation of German law.
... So if VirusTotal shares with everybody, wouldn't somebody trying to keep a backdoor secret be stupid to upload it there?
Yes. That's why professional malware authors use black market multi-scanners.
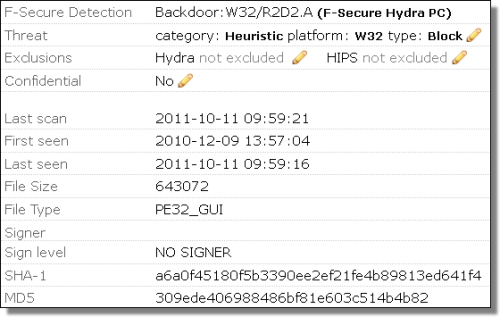
... Link (0 comments) ... Comment
Topic: SECURITY - on September 28, 2011 at 11:16:00 AM CEST
VPN-Dienstleister half mutmaßliches LulzSec-Mitglied zu ermitteln
Der britische VPN- und Web-Proxy-Dienstleister Hide my ass (HMA) hat nach eigenen Angaben dabei mitgewirkt, das mutmaßliche Mitglied der Hackergruppe LulzSec zu identifizieren, das diese Woche vom FBI verhaftet wurde. Das Unternehmen sei der Aufforderung eines britischen Gerichts gefolgt und habe die IP-Adresse des Verdächtigen herausgegeben, unter der er sich bei HMA angemeldet hatte.
... Link (0 comments) ... Comment
Topic: SECURITY - on September 28, 2011 at 11:13:00 AM CEST
Trolls Don't Need To Be Anonymous, And Not All Anonymous People Are Trolls
Julian Sanchez points us to the latest in a series of ridiculously uninformed editorials whining about the evils of anonymity online. This one is by Gayle Falkenthal in the Washington Times. The premise, apparently, is that anonymity only made sense in the past, when the internet was "immature."
When the Internet was new, its nature bred the protective philosophy of embracing anonymity as a counterweight to the potential for sacrificing some of your personal privacy to participate.
The Internet has matured. Anonymity has become counterproductive and even damaging. If you’re willing to stand up and render a public opinion, you should reveal your identity. The time has come to limit the ability of people to remain anonymous. </p>
... Link (0 comments) ... Comment
Topic: SECURITY - on September 28, 2011 at 9:52:00 AM CEST
Anonymes Handeln muss auch im Internet möglich sein
In der vergangenen Woche haben wir über ein Papier des Arbeitskreis Innen in der CDU / CSU Bundestagsfraktion gebloggt, in dem anonyme Kommunikation im Netz von Innenpolitikern wie Hans-Peter Uhl und Wolfgang Bosbach abgelehnt wird: Eine anonyme Teilhabe am politischen Meinungs- und Willensbildungsprozess ist abzulehnen.
Heute überrascht eine Pressemitteilung des stellvertretenden Vorsitzenden der CDU/CSU-Bundestagsfraktion Michael Kretschmer, der das anders formuliert (Die finde ich nicht online, wurde per Mail verschickt):
... Link (0 comments) ... Comment










