Topic: SECURITY - on January 12, 2012 at 1:55:00 PM CET
Iran’s Flying Saucer Downed U.S. Drone, Engineer Claims
Late last month, Iran put on display what it insisted was a captured American stealth drone. At the time, Tehran claimed it brought down the RQ-170 with a sophisticated electronic attack. Nonsense, says one Iranian engineer who claims to have inside knowledge of the drone-nab. The Islamic Republic used force fields and flying saucers to subdue and capture the unmanned aircraft.
Meet Mehran Tavakoli Keshe, who purports to be the father of the RQ-170 abduction. In a recent post to his eponymous foundation’s online forums, Keshe claims the Iranians used “advanced space technology” that he pioneered. “The craft has been air-picked-up and been put down on its belly through the use of field forces,” Keshe writes — by which he means force fields. It’s feeling a lot like Tinfoil Tuesday, our weekly round-up of the planet’s most insane conspiracy theories.
... Link (0 comments) ... Comment
Topic: SECURITY - on January 12, 2012 at 1:10:00 PM CET
US killer spy drone controls switch to Linux
The control of US military spy drones appears to have shifted from Windows to Linux following an embarrassing malware infection.
Ground control systems at Creech Air Force Base in Nevada, which commands the killer unmanned aircraft, became infected with a virus last September. In a statement at the time the Air Force dismissed the electronic nasty as a nuisance and said it posed no threat to the operation of Reaper drones, but the intrusion was nonetheless treated seriously.
"The ground system is separate from the flight control system Air Force pilots use to fly the aircraft remotely; the ability of the pilots to safely fly these aircraft remained secure throughout the incident," it said.
... Link (0 comments) ... Comment
Topic: SECURITY - on January 12, 2012 at 12:21:00 PM CET
Bundesregierung testet Spionagesoftware FinSpy als Ersatz für Bundestrojaner
Die Demokratisierungswelle des „arabischen Frühlings“ hat auch die Debatte um die demokratiefördernde Wirkung des Internets neu entfacht. Im Zuge dieser Debatte, die jüngst auch vor dem Hintergrund der Diskussion um den Einsatz des „Bundestrojaners“ geführt wurde, sind auch solche Unternehmen verstärkt in den Fokus der Öffentlichkeit gerückt, deren ins Ausland gelieferte Programme helfen, Kommunikation via E-Mail, in sozialen Netzwerken und in Blogs zu kontrollieren oder gar ganz verstummen zu lassen.
Seit langem fordere ich gemeinsam mit Malte Spitz und anderen die Bundesregierung dazu auf, nicht länger die Augen vor diesen unethischen Geschäften zu verschließen, sondern endlich eine dringend gebotene Reform der überholten Rüstungsexportrichtlinien vorzunehmen und sich auch dafür einzusetzen, „Dual-use-Güter“ und entsprechende Techniken zur Störung, Überwachung und Unterbrechung des Internet- und Mobilfunkverkehrs endlich in die entsprechenden Export-Bestimmungen aufzunehmen.
gruen-digital.de Remote Monitoring & Infection Solutions: FINSPY MOBILE
... Link (0 comments) ... Comment
Topic: SECURITY - on January 12, 2012 at 9:44:00 AM CET
FBI OpenBSD Backdoors and RSA Cipher Vulnerability
Here is a follow up to the FBI / OpenBSD / OCF encryption backdoors thread as promised. We had a three alarm fire at our house over the Christmas holidays and I am just now getting plugged back in.
-
At ~1997 or thereabouts, the FBI approached a fellow by the name of Lew Jenkins, the Chairman and CEO of Premenos Technology Corp., about their development of an Electronic Data Interchange (EDI) software suite used for corp-to-corp EDI transactions called "Templar".
-
At that point in time encryption technology (especially public key encryption algorithms) were still considered munitions by the United States government, and presumably the FBI was interested in Premenos research related to key escrow and session recovery of RSA-encrypted communication sessions.
... Link (0 comments) ... Comment
Topic: SECURITY - on January 11, 2012 at 2:34:00 PM CET
Adobe plugs critical Reader X security holes
Adobe fixes six serious vulnerabilities that expose Windows and Mac OS X users to malicious hacker attacks.
... Link (0 comments) ... Comment
Topic: SECURITY - on January 11, 2012 at 1:15:00 PM CET
Verfassungsrichter warnt vor geplanter EU-Datenschutzverordnung
Verfassungsrichter Johannes Masing äußert in einem Beitrag für die Süddeutsche Zeitung die Befürchtung, dass mit der geplanten Neuregelung des Datenschutzes auf EU-Ebene nationale Grundrechte nicht mehr anwendbar seien. Das Verfassungsgericht selbst müsse seine Kontrollfunktion in wesentlichen Bereichen aufgeben, in denen es "weit über die Grenzen hinaus als vorbildlich geltende freiheitliche Strukturen geschaffen hat", mahnt der Jurist.
Offiziell will Justizkommissarin Viviane Reding den Verordnungsentwurf erst am 25. Januar vorlegen. Masing betont, dass die allgemeine EU-Datenschutzrichtlinie von 1980 durch eine Verordnung ersetzt werden solle, die einem europaweiten Gesetz gleichkomme. Anders als eine Richtlinie wirke sie unmittelbar, lasse keine Umsetzungsspielräume und verdränge jede Form bereits in Mitgliedsstaaten geschaffenen einschlägigen Rechts. Dies beziehe sich sogar auf das Grundgesetz.
... Link (0 comments) ... Comment
Topic: SECURITY - on January 10, 2012 at 11:18:00 AM CET
US-Großbanken schmieden Allianz gegen Hacker
Amerikas Finanzbranche fürchtet einen Großangriff aus dem Cyberspace. Experten von Morgan Stanley, Goldman Sachs und Co. fahnden jetzt gemeinsam nach Strategien gegen Hacker. Die Attacken werden für die Geldindustrie zu einer ernsten Bedrohung.
Aktion Aurora war nur der Anfang. Vor gut neun Monaten sollen sich Hacker unter anderem Zugriff zum Computernetzwerk von Morgan Stanley verschafft haben. Sie pflanzten offenbar Schadsoftware in das Netzwerk der Großbank ein, mit deren Hilfe sich geheime Daten und interne Kommunikationen ausspähen lassen. Der Fall birgt Brisanz: Die Bank berät Unternehmen bei milliardenschweren Übernahmen. Verschwiegenheit ist dabei oberste Pflicht.
... Link (0 comments) ... Comment
Topic: SECURITY - on January 8, 2012 at 12:55:00 PM CET
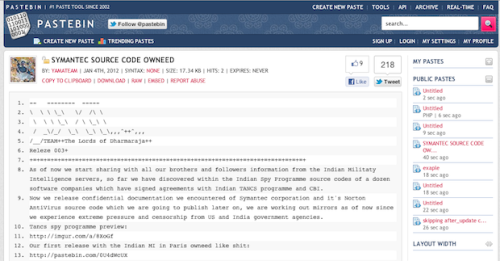
Symantec confirms hacker theft of Norton anti-virus source code
Summary: Symantec, the anti-virus maker, has confirmed that a hacking group has stolen a “segment” of its flagship product. The group said it would make the source code available.
Symantec has confirmed that a “segment” of its flagship Norton anti-virus product’s source code was leaked onto the web this week.
The firm said that the code relates to two older enterprise products, one of which is no longer in production. But it said the breach was on a third-party network rather than its own, and will “not affect any current Norton product”.
... Link (0 comments) ... Comment
Topic: SECURITY - on December 30, 2011 at 11:46:00 AM CET
28C3: Your Disaster/Crisis/Revolution just got Pwned
People are using technology to try to save the world, whether in the disaster response world, or in activist or revolutionary work. Many of the people involved are not technologists. Many of the people building tools for these situations do not understand security. This is a problem because: Privacy issues for disaster response Creepy uncle Creepy government agency Gaming the aid process with crowdsourced reports Activists and revolutionaries are subject to direct attack, coercion, harrassment, etc.
... Link (0 comments) ... Comment
Topic: SECURITY - on December 30, 2011 at 11:10:00 AM CET
28c3: Print Me If You Dare
We first present several generic firmware modification attacks against HP printers. Weaknesses within the firmware update process allows the attacker to make arbitrary modifications to the NVRAM contents of the device. The attacks we present exploit a functional vulnerability common to all HP printers, and do not depend on any specific code vulnerability. These attacks cannot be prevented by any authentication mechanism on the printer, and can be delivered over the network, either directly or through a print server (active attack) and as hidden payloads within documents (reflexive attack).
... Link (0 comments) ... Comment
Topic: SECURITY - on December 30, 2011 at 10:46:00 AM CET
28C3: Wiki "Bugged Planet" verwanzt die Überwachungsindustrie
Projekt sammelt Infos zu Firmen, die Überwachungssoftware an Diktaturen liefern
In seiner Eröffnungsrede zur diesjährigen Hacker-Konferenz 28C3 in Berlin forderte Autor Evgeny Morozov sein Publikum auf, einmal den Spieß umzudrehen und die Überwachungsindustrie zu überwachen. Sie sollten sich von westlichen Konzernen, die Überwachungstechnologien an Diktaturen liefern, anheuern lassen.
... Link (0 comments) ... Comment
Topic: SECURITY - on December 29, 2011 at 5:11:00 PM CET
28C3: How governments have tried to block Tor - Jacob Appelbaum Roger Dingledine
Roger Dingledine and Jacob Appelbaum will talk about how exactly these governments are doing the blocking, both in terms of what signatures they filter in Tor (and how we've gotten around the blocking in each case), and what technologies they use to deploy the filters -- including the use of Western technology to operate the surveillance and censorship infrastructure in Tunisia (Smartfilter), Syria (Bluecoat), and other countries. We'll cover what we've learned about the mindset of the censor operators (who in many cases don't want to block Tor because they use it!), and how we can measure and track the wide-scale censorship in these countries. Last, we'll explain Tor's development plans to get ahead of the address harvesting and handshake DPI arms races.
... Link (0 comments) ... Comment










