Topic: SECURITY - on July 31, 2016 at 12:09:00 PM CEST
The Details About the CIA's Deal With Amazon
A $600 million computing cloud built by an outside company is a "radical departure" for the risk-averse intelligence community.
The intelligence community is about to get the equivalent of an adrenaline shot to the chest. This summer, a $600 million computing cloud developed by Amazon Web Services for the Central Intelligence Agency over the past year will begin servicing all 17 agencies that make up the intelligence community. If the technology plays out as officials envision, it will usher in a new era of cooperation and coordination, allowing agencies to share information and services much more easily and avoid the kind of intelligence gaps that preceded the Sept. 11, 2001, terrorist attacks. For the first time, agencies within the intelligence community will be able to order a variety of on-demand computing and analytic services from the CIA and National Security Agency. What’s more, they’ll only pay for what they use.
... Link (0 comments) ... Comment
Topic: SECURITY - on July 30, 2016 at 5:56:00 PM CEST
Snowden vs Assange
What’s gotten into Edward Snowden? The National Security Agency leaker is criticizing his fellow disseminaters of classified information at WikiLeaks, tweeting that “their hostility to even modest curation is a mistake” and suggesting that some truly damaging material shouldn’t be leaked indiscriminately to the public. Given Snowden’s past collaboration with the group, his words are being treated as surprising by some in the press — evidence of dissension within the largely unified ranks of international transparency crusaders. “Even Edward Snowden disagrees with WikiLeaks,” marvels Fast Company. “Is WikiLeaks alienating its friends,” asks Bloomberg, calling the former NSA contractor “a natural ally … if there’s ever been one.”
... Link (0 comments) ... Comment
Topic: SECURITY - on July 26, 2016 at 11:00:00 AM CEST
ArchStrike Ethical Hacking Linux Operating System Gets Its First ISO Builds
The ArchStrike developers have announced today, July 25, 2016, that their Arch Linux-based operating system designed for ethical hackers now has official installation mediums as ISO images. For those not familiar with all this, ArchStrike was previously known as ArchAssault, of course, still based on the renowned, lightweight and highly customizable Arch Linux distribution. However, the goal of the project is to be a security layer to Arch Linux, offering a collection of over 1,200 security-oriented tools to ethical hackers and security researchers.
... Link (0 comments) ... Comment
Topic: SECURITY - on July 20, 2016 at 4:37:00 PM CEST
Hacker ‘Phineas Fisher’ Speaks on Camera for the First Time—Through a Puppet
A little bit over a year ago, the normally quiet Twitter account of Hacking Team, an Italian company that sells spying tools to governments all over the world, started acting weird. “Since we have nothing to hide, we’re publishing all our e-mails, files, and source code,” read a Tweet published on late Sunday, July 5, 2015. The tweet was accompanied by a link to a torrent file of around 400 gigabytes, practically everything Hacking Team had on its corporate servers: internal emails, confidential documents, and even the company’s source code. Hacking Team, which at that point was already notorious for selling its wares to repressive regimes and governments such as Ethiopia, Morocco, and others, had just gotten hacked.
... Link (0 comments) ... Comment
Topic: SECURITY - on July 15, 2016 at 10:54:00 AM CEST
Hackers steal millions from ATMs without using a card
Taiwan is trying to figure out how hackers managed to trick a network of bank ATMs into spitting out millions. Police said several people wearing masks attacked dozens of ATMs operated by Taiwan's First Bank on Sunday. They spent a few minutes at each of the machines before making off with the equivalent of $2 million stashed in a backpack. They didn't use bank cards but rather appeared to gain control of the machines with a "connected device," possibly a smartphone, the police said in a statement Thursday. Authorities are now hunting the thieves, who they say came from Russia and eastern Europe. The ATMs were made by German manufacturer Wincor Nixdorf (WNXDY). The company confirmed that several of its machines in Taiwan were hacked in a "premeditated attack."
... Link (0 comments) ... Comment
Topic: SECURITY - on July 14, 2016 at 3:57:00 PM CEST
FBI Agent: Decrypting Data ‘Fundamentally Alters’ Evidence
An FBI agent has brought up an interesting question about the nature of digital evidence: Does decrypting encrypted data “fundamentally alter” it, therefore contaminating it as forensic evidence? According to a hearing transcript filed last week, FBI Special Agent Daniel Alfin suggested just that. The hearing was related to the agency's investigation into dark web child pornography site Playpen. In February 2015, the FBI briefly assumed control of Playpen and delivered its users a network investigative technique (NIT)—or a piece of malware—in an attempt to identify the site's visitors.
... Link (0 comments) ... Comment
Topic: SECURITY - on July 14, 2016 at 3:50:00 PM CEST
Tor-Projekt tauscht Aufsichtsgremium aus
Relativ überraschend hat das Anonymisierungs-Projekt seinen Verwaltungsrat komplett ausgetauscht. Unter den neuen Direktoren ist auch Kryptografie-Ikone Bruce Schneier. Der Anonymisierungsdienst Tor hat sein Aufsichtsgremium komplett ausgetauscht. Der alte, siebenköpfige Verwaltungsrat habe einstimmig sechs neue Mitglieder bestimmt und sei zugleich geschlossen zurückgetreten. Zur neuen, ehrenamtlich tätigen Führungsspitze zählen unter anderem Cindy Cohn, die Leiterin der Electronic Frontier Foundation, sowie die prominenten Kryptologen Bruce Schneier und Matt Blaze.
... Link (0 comments) ... Comment
Topic: SECURITY - on July 14, 2016 at 3:47:00 PM CEST
The Tor Project Elects New Board of Directors
Today, the board of directors of the Tor Project is announcing a bold decision in keeping with its commitment to the best possible health of the organization. Says Tor's Executive Director Shari Steele, "I think this was an incredibly brave and selfless thing for the board to do. They’re making a clear statement that they want the organization to become its best self."
... Link (0 comments) ... Comment
Topic: SECURITY - on July 13, 2016 at 12:02:00 PM CEST
Riffle: MIT Creates New Anonymity Network Which Is More Secure Than TOR
MIT is a place where a stone thrown up in the air will definitely land on an extraordinary mind. I have no intention to hurt those guys, by the way. The point of giving such example is that the researchers at MIT have come up with a new anonymity network which is said to be more secure and safer than the existing ones, namely Tor. The news sounds good to the ears after hearing stories about vulnerabilities present in Tor. MIT News reports that the newly created anonymity network will be uncovered by the researchers of the MIT Computer Science and Artificial Intelligence Lab and the École Polytechnique Fédérale de Lausanne at the Privacy Enhancing Technologies Symposium later this month.

... Link (0 comments) ... Comment
Topic: SECURITY - on July 13, 2016 at 11:52:00 AM CEST
Sophisticated Malware Found on the Network of a European Energy Company
Security researchers from SentinelOne have stumbled upon a malware campaign targeting at least one European energy company, which features a large arsenal of tools rarely seen in ordinary malware samples. The detail that particularly stood out as regards the malware's code was the fact that its creators spent a great amount of time to make sure their threat wouldn't raise any flags on infected hosts. This level of detail and attention is usually found in the malware used by nation states. SentinelOne experts believe that a threat actor residing in Eastern Europe may have been behind this malware, which they dubbed Furtim's Parent.
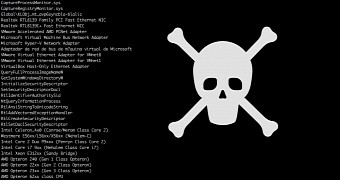
... Link (0 comments) ... Comment
Topic: SECURITY - on July 13, 2016 at 11:42:00 AM CEST
The FBI Says Its Malware Isn’t Malware Because the FBI Is Good
The FBI is facing accusations that malware it deployed while running Operation Playpen, a sting that infiltrated and maintained a dark web child pornography website for two weeks and eventually led to more than 100 arrests, was illegal. But the agency swears that using malware was good because, well, the FBI had good intentions. Some judges have actually ruled to throw out evidence obtained by the malware the FBI used on the basis that it did not have the proper warrants. (The DOJ and FBI just had a major breakthrough with the supreme court in modifying Rule 41, giving them expansive new hacking powers, but we’ll get to that in a second.) According to a legal brief filed by they FBI, “A reasonable person person or society would not interpret the actions taken by a law enforcement officer pursuant to a court order to be malicious.” Hmm.
... Link (0 comments) ... Comment
Topic: SECURITY - on July 12, 2016 at 4:48:00 PM CEST
Two Factor Auth (2FA)
List of websites and whether or not they support 2FA.
... Link (0 comments) ... Comment










