Topic: WEB - on August 20, 2016 at 11:29:00 AM CEST
Ten years later! - YOU SUCK
... Link (0 comments) ... Comment
Topic: Appelbaum - on August 20, 2016 at 10:25:00 AM CEST
The Weaponising Of Social Part 3: The Resurrection Of IOError
The genesis of this groundbreaking series was a moral obligation to highlight obvious discrepancies in the coordinated smears against Jacob Appelbaum (IOError). That smear campaign’s self-pronounced and ostensibly achieved aim was to permanently shut down his (anti-surveillance, anti-three-letter-agency) public speaking by casting him out from the very communities he has dedicated his life to supporting.
... Link (0 comments) ... Comment
Topic: FUN - on August 18, 2016 at 6:08:00 PM CEST
GoPro Hot Wheels Car Goes on Epic Joyride
... Link (0 comments) ... Comment
Topic: Netz - on August 18, 2016 at 6:04:00 PM CEST
GitHub Universe Big Bang Benefit Concert
You've never been to an after party like this. We’re doing something a little different with our conference after party and opening it up to GitHub communities outside of our conference attendees. The Big Bang brings together the community to support and celebrate an organization shaping the future of software, Black Girls Code. Featuring two extraordinary acts in the historic Masonic Auditorium, The Big Bang unites Universe attendees and the broader Bay Area community. The concert is free for all Universe badge holders and open to the public for a $40 donation. All tickets are general admission seating. Event Details Wednesday, September 14 at The Masonic, 1111 California Street, San Francisco, CA. Doors will open at 8pm. Light snacks will be served, and a cash bar will be available.

... Link (0 comments) ... Comment
Topic: Space - on August 18, 2016 at 6:02:00 PM CEST
This ancient text reveals a Maya astronomer calculated the movements of Venus over a millennium ago
A new analysis of the ancient Mayan text, the Dresden Codex – the oldest book written in the Americas known to historians – suggests an early Maya scientist may have made a major discovery in astronomy more than a thousand years ago. According to a new study, astronomical data written in part of the text called the Venus Table weren't just based on numerology as had been thought, but were a pioneering form of scientific record-keeping that had huge significance for Maya society. "This is the part that I find to be most rewarding, that when we get in here, we're looking at the work of an individual Mayan, and we could call him or her a scientist, an astronomer," says anthropologist Gerardo Aldana from University of California, Santa Barbara. "This person, who's witnessing events at this one city during this very specific period of time, created, through their own creativity, this mathematical innovation."
... Link (0 comments) ... Comment
Topic: SCIENCE - on August 18, 2016 at 5:57:00 PM CEST
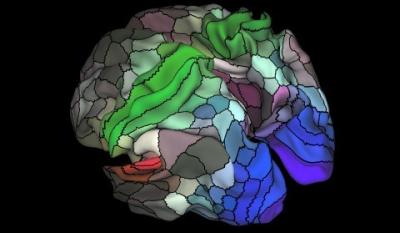
Putting a computer in your brain is no longer science fiction
Like many in Silicon Valley, technology entrepreneur Bryan Johnson sees a future in which intelligent machines can do things like drive cars on their own and anticipate our needs before we ask.
What’s uncommon is how Johnson wants to respond: find a way to supercharge the human brain so that we can keep up with the machines. From an unassuming office in Venice Beach, his science-fiction-meets-science start-up, Kernel, is building a tiny chip that can be implanted in the brain to help people suffering from neurological damage caused by strokes, Alzheimer’s or concussions. Top neuroscientists who are building the chip — they call it a neuroprosthetic — hope that in the longer term, it will be able to boost intelligence, memory and other cognitive tasks.
... Link (0 comments) ... Comment
Topic: DRUGS - on August 18, 2016 at 5:47:00 PM CEST
A cannabis product is being tested by the NHS
An NHS unit is testing a cannabidiol vaporiser, the first cannabis product ever tested by the public body, which could hugely impact surrounding UK legislation if its medical benefits can be evidenced. In a report by the Independent, they found that the producers of MediPen had been consulting with NHS production and regulatory support pharmacists in the last few months as they test cannabis oil formulation and its properties.

... Link (0 comments) ... Comment
Topic: DRUGS - on August 18, 2016 at 5:45:00 PM CEST
The DEA Says Weed Should Stay Illegal Because If You Smoke It You'll Get Arrested
What’s so bad about weed that we should continue to keep it illegal in this country? The DEA is glad you asked. We should keep weed illegal because it is illegal, they say. One of the dangers of weed is that if you smoke it, you might get arrested is an impressive bit of tautological reasoning, which comes from The DEA Position on Marijuana, a 2011 document recently obtained by MuckRock in response to a FOIA request. The document puts forth the agency’s arguments for why we should continue weed prohibition at the federal level. The whole thing is worth a read—it also includes an anecdote about using pot to treat an ecstasy overdose as supposed evidence that it has no medical value—but one bullet point sticks out in particular. Under the heading DANGERS OF MARIJUANA, it reads:
... Link (0 comments) ... Comment
Topic: DRUGS - on August 18, 2016 at 5:40:00 PM CEST
Where does all that Colorado pot tax go?
Colorado is pulling in a significant amount of money by taxing recreational marijuana, but it’s not enough to pave the streets in gold. In part because supporters of legal pot hyped the potential to raise millions, some Coloradans have been left to wonder why all that money hasn’t revolutionized life in our state.
$30.00 – 1/8 oz marijuana $3.00 – 10% special state sales tax $0.87 – 2.9% regular state sales tax $1.43 – 4.75% regular Denver sales tax (including RTD/SCFD tax) $1.05 – 3.5% special Denver sales tax
$36.35 – GRAND TOTAL
... Link (0 comments) ... Comment
Topic: SECURITY - on August 18, 2016 at 5:17:00 PM CEST
‘Shadow Brokers’ Claim to be Selling NSA Malware, in What Could Be Historic Hack
A mysterious online group calling itself “The Shadow Brokers” is claiming to have penetrated the National Security Agency, stolen some of its malware, and is auctioning off the files to the highest bidder. The authenticity of the files cannot be confirmed but appear to be legitimate, according to security researchers who have studied their content. Their release comes on the heels of a series of disclosures of emails and documents belonging mostly to Democratic officials, but also to Republicans. Security researchers believe those breaches were perpetrated by agents thought to be acting on behalf of Moscow.
foreignpolicy.com Equation Group - Cyber Weapons Auction Shadow Brokers: NSA Exploits of the Week Hackers Say They Hacked NSA-Linked Group, Want 1 Million Bitcoins to Share More Hackers Claim to Auction Data They Stole From NSA-Linked Spies Shadow Brokers Group Auctions Off Supposed NSA Hacking Tool NSA HACKED!!! Multiple Hacking Tools And Exploits Leaked Online
... Link (0 comments) ... Comment
Topic: SECURITY - on August 16, 2016 at 4:33:00 PM CEST
WikiLeaks Published a Bunch of Malware Together with the Turkey AKP Emails
The WikiLeaks dump of emails stolen from the server of AKP, Turkey's ruling party, contains hundreds of links to downloadable malware, Bulgarian security researcher Vesselin Bontchev has discovered. The researcher, who works at the National Laboratory of Computer Virology at the Bulgarian Academy of Sciences in Sofia, Bulgaria, has created a script that parsed the WikiLeaks AKP email data dump for links and sent them for scanning via VirusTotal's API. Bontchev initially discovered around 80 links pointing to malware downloads, which he presented in a report he later amended and now lists 323 samples.
... Link (0 comments) ... Comment
Topic: FUN - on August 16, 2016 at 4:29:00 PM CEST
Monty Pythons Argument-Clinic auf 2 alten Speech Synthesizern
Michael Palin is played by the Dectalk Express (Perfect Paul modified to sound more like Stephen Hawking)
John Cleese is played by the Intex Talker (Votrax SC-01A)
... Link (0 comments) ... Comment










